An empirical analysis of anonymity in Zcash
Summary of paper review
Bitcoin offers little in the way of anonymity. Zcash was carefully designed with privacy in mind. In theory, users can remain anonymous. In practice, it depends on how they interact with Zcash.
Zcash guarantees and the shielded pool
Zcash is based on highly regarded research including a cryptographic proof of its main privacy feature, the shielded pool.
All newly generated coins are required to pass through the shielded pool.
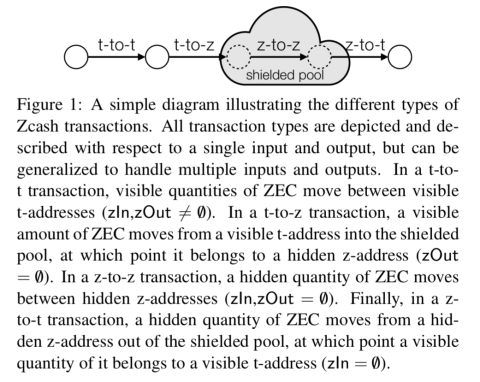
To support transparent (sender/receiver pseudonyms visible) and shielded transactions, Zcash supports two types of addresses: transparent addresses (t-address) and shielded addresses (z-address). This leads to four classes of transactions:
- transparent transactions from t-address to t-address
- shielded transactions from t-address to z-address
- deshielded transactions from z-address to t-address
- private transactions from z-address to z-address
Four actors in the Zcash ecosystem:
- founders receive 20% of all newly generated coins
- miners maintain the ledger and receive block rewards and transaction fees
- services accept ZEC as a form of payment (ex. exchanges and trading platforms)
- individual participants hold and transact ZEC at a personal level
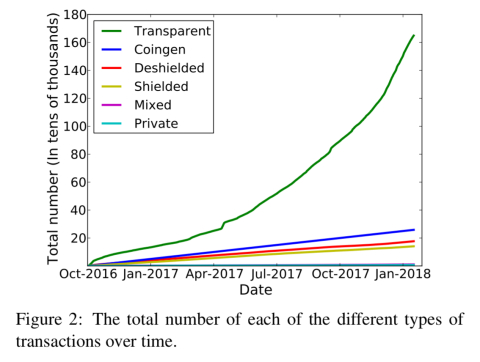
Transparent transactions are growing over time. They offer the same privacy of Bitcoin (ie. not great).
Heuristics
Use heuristics similar to those used in de-anonymising Bitcoin transactions:
- if two or more t-addresses are inputs in the same transaction (for transparent, shielded, mixed transactions), then they are controlled by the same entity
- if one or more addresses is an input t-address in a vJoinSplit transaction and a second address is an output t-address in the same vJoinSplit transaction, then if the size of zOut is 1 (ie. this is the only transparent output address), the second address belongs to the same user who controls the input address.
Using heuristic 1 identifies clusters of addresses. Attaching an entity to any element in the cluster associates that cluster with the entity.
Publicised addresses of founders and mining pools also act as seeds to discover larger cluster of addresses.
Who uses the shielded pool?
Shielded pool deposits and withdrawals closely mirror eachother. This means most users withdraw the same amount they deposited into the shielded pool very quickly after the deposit. Most of the people putting money into the pool are miners, since new coins must go through the pool.
If a t-to-z transaction can be linked to a z-to-t transaction, then those coins are out of the anonymity set.
Founders have a predictable behaviour. We know they deposit 249.9999 ZEC (the reward for 100 blocks) from their known addresses. They also like to make withdrawals of 250.0001 ZEC. Heuristic 3:
- any z-to-t transaction carrying 250.0001 ZEC is done by founders
This helps identify another 48 founder addresses.
Miners are predictable too, since deposits immediately follow coin generation. Heuristic 4:
- if a z-to-t transaction has over 100 output t-addresses, one of which belongs to a known mining pool, then label the transaction as a mining withdrawal associated to that pool, and label all non-pool output t-addresses as belonging to miners
This identifies 110,918 addresses as belonging to miners, linking a significant portion of z-to-t transactions.
Unrelated to miners and founders, exactly one t-to-z transaction of value v followed by exactly one z-to-t transaction of the same value within a small number of blocks can be linked.
The shadow brokers
Using heuristics and looking at deposits matching the price of NSA tool dumps made by the hacker collective “The Shadow Brokers” (TSB), the authors were able to identify 24 clusters potentially associated with TSB.
Conclusion
our study has shown that most users are not taking advantage of the main privacy features of Zcash at all. Furthermore, the participants who do engage with the shielded pool do so in a way that is identifiable, which has the effect of significantly eroding the anonymity of other users by shrinking the overall anonymity set.